WordPress security issues affect millions of websites annually, with most attacks targeting preventable vulnerabilities rather than sophisticated exploits.
The vast majority of WordPress vulnerabilities originate from plugins and themes, not the core software itself. These security issues typically result from basic oversights: outdated software, weak passwords, and missing security measures that leave sites defenseless against common attacks.
Understanding these ten critical vulnerabilities helps identify and address the most dangerous threats facing your WordPress website today.
WordPress Security Issues at a Glance
- Outdated WordPress Core, Themes, and Plugins
- Weak Passwords and User Authentication
- SQL Injection Vulnerabilities
- Cross-Site Scripting (XSS) Attacks
- File Permissions and Directory Access Issues
- Lack of SSL Certificate and HTTPS
- Default Admin Username and Login URL
- XML-RPC Vulnerabilities
- Malicious Themes and Plugins
- Lack of Regular Backups
1. Outdated WordPress Core, Themes, and Plugins
The most common cause of WordPress security breaches is outdated software. A 2023 Sucuri report found that about 39% of hacked CMS sites were running outdated core software at the time of infection. The 2024 Patchstack security report found that 97% of new WordPress vulnerabilities originated in plugins, while only 0.2% were related to core WordPress itself. Failing to update even a single plugin or theme can expose your entire site to compromise
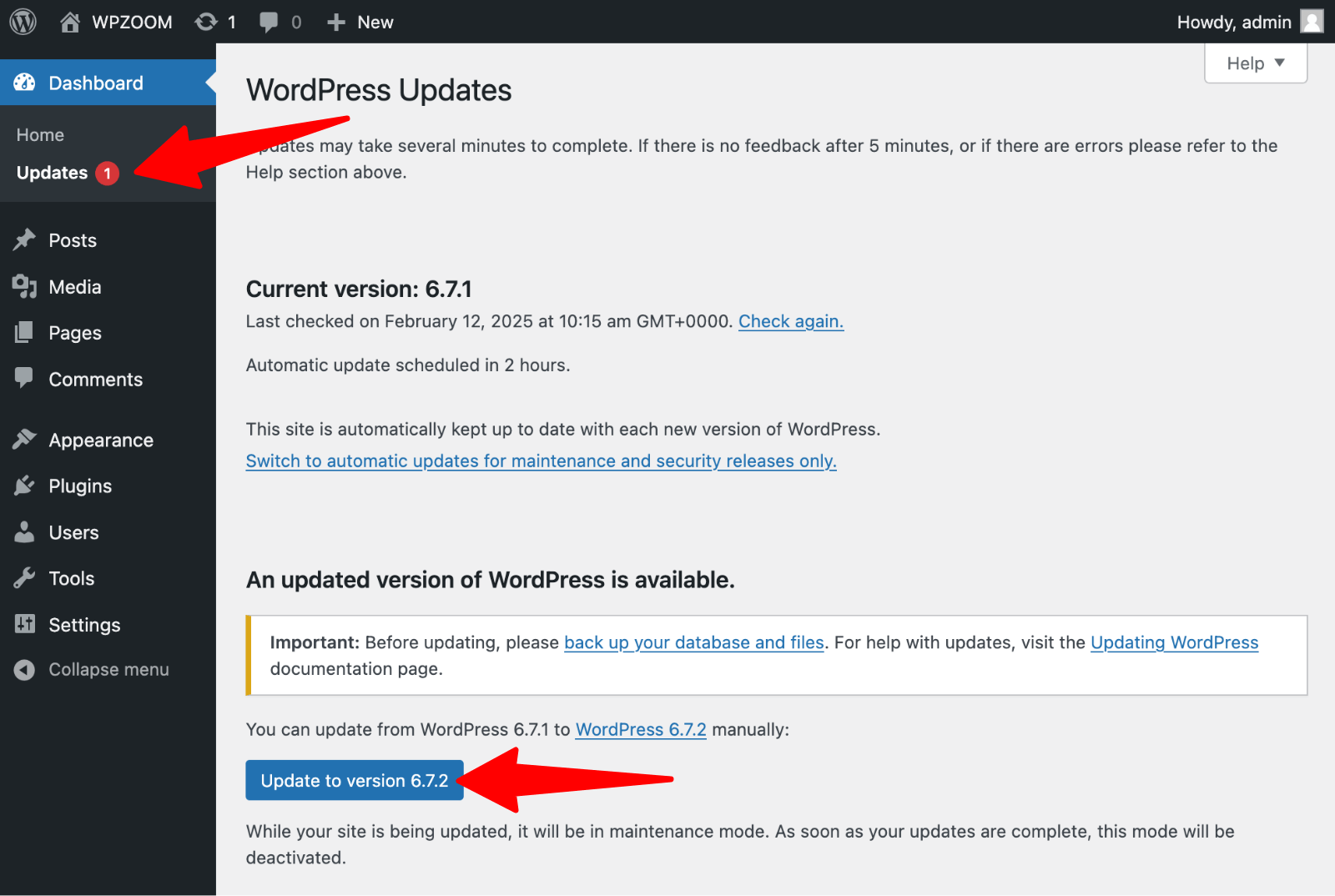
Every WordPress update includes critical security patches addressing newly discovered vulnerabilities. When you delay updates, you’re essentially leaving known security holes wide open for attackers to exploit. Hackers actively scan the internet for sites running vulnerable versions, using automated tools that can compromise thousands of sites within hours of a vulnerability becoming public.
Consider the infamous WordPress REST API vulnerability discovered in 2017. Within days of its disclosure, over 1.5 million pages were defaced by attackers exploiting sites that hadn’t updated to WordPress 4.7.2. The fix was simple—a one-click update—yet millions of site owners learned this lesson the hard way.
Solution:
Implement a robust update management strategy:
- Enable automatic updates for WordPress core and trusted plugins.
- Update plugins and themes within 48 hours of release.
- For themes and critical plugins, test updates on a staging site first.
- Create a weekly routine to check for updates, and subscribe to WordPress security bulletins to stay informed about critical patches.
- Remove unused themes and plugins entirely.
- Document all installed plugins and their purposes.
2. Weak Passwords and User Authentication
Weak passwords remain one of the most exploited WordPress security risks. According to cybersecurity industry reports, 81% of hacking-related breaches involve compromised, weak, or reused passwords. Poor password practices remain one of the top causes of website hackings, and WordPress sites are no exception. Attackers use sophisticated brute force tools that can try millions of password combinations per hour.
The problem extends beyond simple passwords like “123456” or “password.” Even seemingly complex passwords can be vulnerable if they’re based on dictionary words, personal information, or common patterns. Attackers also leverage massive databases of previously leaked passwords, trying these known combinations across multiple sites.
WordPress’s default authentication system, while functional, lacks advanced security features out of the box. Without additional protection, your login page remains exposed to unlimited login attempts, making it only a matter of time before a determined attacker gains access.
Solution:
Implement a multi-layered authentication approach:
- Enforce strong password policies requiring at least 12 characters with a mix of uppercase, lowercase, numbers, and special characters. Better yet, use passphrases—longer, memorable sentences that are virtually impossible to crack.
- Enable two-factor authentication (2FA) using plugins like Wordfence or Google Authenticator, adding an extra security layer even if passwords are compromised.
- Consider implementing login attempt limits and temporary lockouts after failed attempts.
- Hide login error messages that reveal whether a username exists, and consider changing your login URL from the default /wp-login.php to something unique.
While not foolproof, these measures significantly increase the effort required for successful attacks.
3. SQL Injection Vulnerabilities
SQL injection represents one of the most dangerous WordPress vulnerabilities, allowing attackers to directly manipulate your database. Through carefully crafted malicious input, hackers can bypass authentication, steal sensitive data, modify content, or even delete your entire database.
In WordPress, SQL injection typically occurs through poorly coded plugins or themes that fail to properly sanitize user input. Contact forms, search boxes, and custom query parameters are common entry points. Once exploited, attackers can extract user credentials, payment information, or inject malicious content that affects all site visitors.
The WordPress core team has done excellent work protecting against SQL injection, but the same can’t be said for all third-party developers. A single vulnerable plugin can compromise your entire site, regardless of how secure the rest of your setup might be.
Solution:
- Protect against SQL injection by using WordPress’s built-in database abstraction layer and prepared statements for all database queries.
- When selecting plugins, choose those from reputable developers with regular updates and strong security track records.
- Implement a Web Application Firewall (WAF) that can detect and block SQL injection attempts before they reach your site.
- Regularly scan your site using tools like WPScan or Sucuri SiteCheck to identify potential SQL injection vulnerabilities.
- Keep your database user permissions minimal—your WordPress database user shouldn’t have privileges to drop tables or databases.
- Consider using security plugins like Wordfence or Solid Security that include SQL injection protection as part of their feature set.
4. Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into your WordPress pages, which then execute in visitors’ browsers. These scripts can steal cookies, redirect users to malicious sites, or even take administrative actions on behalf of logged-in users.
XSS attacks in WordPress commonly occur through comment forms, user profile fields, or any area where user input is displayed without proper sanitization. The danger multiplies when administrators are targeted—a successful XSS attack against an admin can lead to complete site takeover.
There are three types of XSS attacks:
- stored (persistent)
- reflected
- DOM-based
Stored XSS, where malicious scripts are saved in your database, poses the greatest threat as it affects all users who view the infected content. Even major plugins have fallen victim to XSS vulnerabilities, affecting millions of sites before patches were released.
Solution:
Implement comprehensive input validation and output encoding throughout your WordPress site.
- Use WordPress’s built-in sanitization functions like esc_html(), esc_attr(), and wp_kses() for all user-generated content.
- Enable Content Security Policy (CSP) headers to restrict which scripts can execute on your pages.
- Install security plugins that include XSS protection and regularly update all themes and plugins, as developers frequently patch XSS vulnerabilities.
- Disable HTML in comments if you don’t need it, and be extremely cautious with plugins that allow users to input or display custom HTML/JavaScript code.
5. File Permissions and Directory Access Issues
Incorrect file permissions create serious WordPress security concerns by potentially allowing unauthorized users to read, modify, or execute files on your server. Many WordPress compromises occur not through sophisticated hacking but through simple permission misconfigurations.
When file permissions are too permissive (like 777), any user on the shared server can potentially access and modify your files. This includes injecting malicious code, stealing sensitive configuration data, or using your server resources for their own purposes. Conversely, overly restrictive permissions can break functionality, leading frustrated users to overcorrect with dangerously open permissions.

The wp-config.php file, containing database credentials and security keys, is particularly sensitive. If accessible to unauthorized users, it provides everything needed to completely compromise your site. Similarly, improperly secured upload directories can become launching pads for malware distribution.
Solution:
Set correct file permissions across your WordPress installation.
- Files should typically be set to 644 (readable by everyone, writable only by the owner), while directories should be 755 (readable and executable by everyone, writable only by the owner).
- The wp-config.php file deserves special attention—set it to 640 or even 600 to restrict access further.
- Never use 777 permissions unless absolutely necessary and only temporarily.
- Use tools like SSH or your hosting control panel’s file manager to audit and correct permissions.
- Many security plugins include file permission scanners that alert you to dangerous configurations.
- Consider moving wp-config.php one directory level above your web root for additional protection.
Upgrade Your Website with a Premium WordPress Theme
Find a theme that you love and get a 10% discount at checkout with the FLASH10 code
Choose your theme
6. Lack of SSL Certificate and HTTPS
Operating a WordPress site without SSL encryption is like leaving your front door wide open. Beyond the obvious WordPress security risks of data interception, the absence of HTTPS affects your search rankings, visitor trust, and even basic functionality as browsers increasingly require encryption for modern features.
Without SSL, all data transmitted between your site and visitors travels in plain text. This includes login credentials, personal information, and payment details. On public WiFi networks, attackers can easily intercept this data using readily available tools. Man-in-the-middle attacks become trivial, allowing hackers to modify content in transit or inject malicious code.
Google has marked non-HTTPS sites as “Not Secure” since 2018, immediately signaling to visitors that your site may be unsafe. This warning alone can devastate conversion rates and credibility. Additionally, many modern WordPress features and third-party services require HTTPS to function properly.
Solution:
Implement SSL immediately—there’s no excuse when free certificates are available through Let’s Encrypt. Most quality hosting providers offer one-click SSL installation.
- After installing your certificate, ensure all resources load over HTTPS by updating your WordPress Address and Site Address in settings.
- Use plugins like Really Simple SSL to handle mixed content issues automatically.
- Don’t stop at basic implementation. Enable HSTS (HTTP Strict Transport Security) to force HTTPS connections and prevent downgrade attacks.
- Consider upgrading to an Extended Validation (EV) certificate for e-commerce sites to display additional trust indicators.
- Regular monitoring ensures your certificate remains valid and properly configured.
7. Default Admin Username and Login URL
Using the default “admin” username is like putting a neon sign on your site saying, “hack me.” Automated bots continuously scan WordPress sites, attempting to log in with common usernames like “admin,” “administrator,” or your domain name. Combined with the standard /wp-login.php URL, you’re making attackers’ jobs remarkably easy.
These predictable configurations enable efficient brute force attacks. Botnets can distribute login attempts across thousands of IP addresses, bypassing simple rate limiting. With the username known, attackers only need to crack your password, cutting their work in half. The standard login URL also exposes your site to unnecessary traffic and potential denial-of-service attacks.
Solution:
- Never use “admin” as a username. During WordPress installation, create a unique administrator username. For existing sites, create a new administrator account with a unique username, log in with it, then delete the old “admin” account, attributing all content to your new user.
- Consider changing your login URL using plugins like WPS Hide Login or through custom code.
This simple change eliminates 99% of automated login attempts. However, remember this is security through obscurity—a supplementary measure, not a primary defense. Combine it with strong passwords, two-factor authentication, and login attempt limiting for comprehensive protection.
8. XML-RPC Vulnerabilities
XML-RPC, a remote procedure call protocol, enables external applications to interact with your WordPress site. While useful for mobile apps and remote publishing, it presents significant WordPress security issues when left unsecured. Many site owners don’t even know it exists, let alone that it’s actively exposing their sites to attacks.
The primary concern is XML-RPC’s authentication bypass potential. Attackers can use the system.multicall method to try hundreds of password combinations in a single request, circumventing traditional rate limiting. This amplification effect makes brute force attacks devastatingly efficient. Additionally, XML-RPC can be exploited for DDoS attacks, using your server to attack other sites.
Solution:
- Unless you specifically need XML-RPC for mobile apps or remote publishing tools, disable it entirely.
- If you need selective XML-RPC functionality, use plugins that allow granular control over which methods remain accessible. Many security plugins include XML-RPC management features.
- For sites requiring XML-RPC, implement additional authentication layers and monitor access logs for suspicious activity.
- Consider modern alternatives like the WordPress REST API, which offers better security controls.
9. Malicious Themes and Plugins
The allure of “free” premium themes and plugins leads thousands of WordPress users into security nightmares annually. These nulled (pirated) themes and plugins often contain backdoors, malware, and encrypted malicious code that can completely compromise your site. Even legitimate-looking items from third-party marketplaces can harbor security threats.
Malicious code in themes and plugins can perform various nefarious activities: creating hidden admin accounts, injecting spam links, stealing customer data, or using your server for cryptocurrency mining. The code is often obfuscated and time-delayed, activating weeks after installation to avoid detection. By then, the damage may be extensive and difficult to reverse.
Solution:
- Only download themes and plugins from trusted sources: WordPress.org repository, directly from established developers like WPZOOM, or reputable marketplaces like ThemeForest (with careful vetting). The few dollars saved on nulled products aren’t worth losing your entire business.
- Before installing any theme or plugin, research the developer, check reviews, and verify update frequency.
- Regularly audit installed plugins—remove any that are abandoned, unnecessary, or from unknown developers.
Quality themes and plugins are investments in your site’s security and sustainability.
10. Lack of Regular Backups
While not a vulnerability itself, the absence of reliable backups transforms any security incident from a temporary setback into a potential catastrophe. WordPress vulnerabilities are constantly discovered, and even the most secure sites can fall victim to zero-day exploits. Without backups, you’re one hack away from losing everything.
Many site owners assume their hosting provider’s backups are sufficient, only to discover limitations when disaster strikes. Hosting backups might be infrequent, incomplete, or inaccessible when you need them most. Worse, if your site is compromised for an extended period, all your backups might be infected, making restoration impossible.
Solution:
- Implement a comprehensive 3-2-1 backup strategy: maintain three copies of your data, store them on two different media types, and keep one copy off-site.
- Use dedicated backup plugins like UpdraftPlus that automate the process and store backups in remote locations like Google Drive, Dropbox, or Amazon S3.
- Schedule backups based on your update frequency—daily for active sites, weekly for others.
- Test restoration procedures regularly; a backup you can’t restore is worthless.
- Maintain multiple backup versions to ensure you can recover from both recent and older compromises.
- Consider managed WordPress hosting with integrated backup solutions for additional peace of mind.
Additional Security Best Practices
Beyond addressing these specific vulnerabilities, implement these overarching security measures:
- Web Application Firewall (WAF): Deploy a WAF through services like Cloudflare or Sucuri to filter malicious traffic before it reaches your site. WAFs block common attack patterns and provide DDoS protection.
- Security Monitoring: Use real-time monitoring tools to detect suspicious activity immediately. Services like Wordfence or MalCare alert you to file changes, failed login attempts, and potential breaches.
- Regular Security Audits: Schedule monthly security scans using tools like WPScan or Sucuri SiteCheck. Address identified issues promptly and document your security measures.
- Principle of Least Privilege: Grant users only the minimum permissions necessary. Regularly review user accounts, removing inactive ones and downgrading permissions where possible.
- Security-Focused Hosting: Choose hosting providers specializing in WordPress security, offering features like isolated accounts, automatic updates, and specialized firewall rules.
Building Security Into Your WordPress Foundation
Security starts with choosing the right foundation for your WordPress site. At WPZOOM, we’ve integrated these security principles into every theme we develop, ensuring clean code, regular updates, and compatibility with leading security plugins.
Our themes undergo rigorous security testing and follow WordPress coding standards to minimize vulnerabilities. When you build on a secure foundation, implementing these additional security measures becomes simpler and more effective. Explore our collection to find your perfect, security-conscious theme today.


